A note on bridges & layer-2 protocols
We, as a community, are incredibly excited about off-chain protocols as a way to scale the network. It allows the majority of transactions to be moved from the layer-1 blockchain to an off-chain system, bypassing all network fees and latency issues on the layer-1 blockchain.
What is a bridge?
In this article, I want to discuss something fundamental for all off-chain protocols. A basic component that is often overlooked, but crucial to assess for the safety of your funds:
A bridge is responsible for holding the assets on a layer-1 blockchain while the same assets are released on another (and external) service. It defines who has custody of the funds and the conditions that must be satisfied before the assets can be unlocked.
In a nutshell, whenever a layer-1 blockchain like Ethereum connects to any other system, there is a bridge being used. All bridges have similar actions:
- Deposit. A user can deposit funds into the bridge and a representation of the assets are issued on the other system,
- Update account balance. The bridge is notified about the new account balances and this can be used to aid the withdrawal process.
- Withdrawal. A user can withdraw their assets from the bridge according to their balance on the other system and the issued tokens are burnt on the other system.
The most common type of bridge (that people use without noticing) is the single-organisation one:

If we simply consider the bridge and nothing else, then we can claim that a cryptocurrency exchange is an off-chain protocol. Users can lock funds into the service, bypass network fees & latency when transacting, and eventually withdraw their funds back to the layer-1 blockchain.
Alongside the single-organisational bridge, there are two other types of bridges that rely upon a set of custodians:
- Multi-organisation bridge. A fixed set of independent parties (K of N) have custody of funds that are locked.
- Crypto-economic bridge. A dynamic set of parties, determined by their weight in assets, have custody of the funds.
A key insight is that all three bridges on the layer-1 blockchain cannot verify the account balances from the other system are correct (or if the liabilities in the other system exceed the assets in the bridge). It is up to the set of custodians to verify that all withdrawals are processed in accordance with the other system. They ultimately dictate whether the funds can be released and who should receive it.
Sidechains and bridges are independent
So far, we have mostly considered a bridge for on-boarding onto a custodial service like a cryptocurrency exchange. An increasingly popular use-case for a bridge is to connect one blockchain to another blockchain (which, by the way, is the origin of the term sidechain).
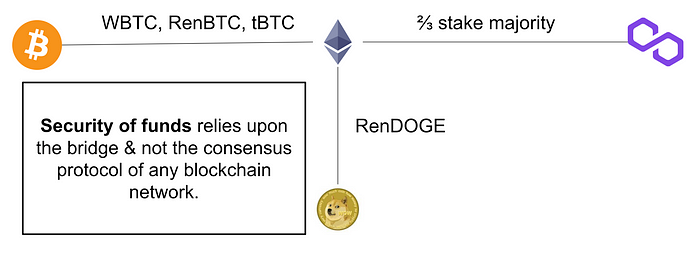
There are several examples of bridges in the wild:
- WBTC: A single-organisational bridge that unlocks BTC onto Ethereum.
- Liquid network or RSK: A multi-organisational bridge, where a federation of parties with HSM lock/unlock funds from BTC to another blockchain.
- Polygon bridge. A crypto-economic bridge, where 2/3+1 stake locked in the bridge periodically agree upon the account balances of all users on Polygon and users can use this agreement to withdraw their funds on Ethereum. (In reality, polygon is ultimately controlled by a small multisig contract, but this example focuses on its long-term goal).
- Rainbow bridge. A crypto-economic bridge, where the bridge contract is a light-client that can verify the progression of the other blockchain. It does not check the validity of the other blockchain & the safety of funds ultimately relies upon the continuous progression of the other blockchain (which is secured via crypto-economics).
Crucially, each bridge has its own security model and it is independent of the blockchain networks. We can take an easy case, WBTC, to further elaborate:
BitGo Trust has custody of funds locked in Bitcoin and they are responsible for issuing the same quantity of WBTC on Ethereum. A smart contract on Ethereum tracks the account balances for all transfers of WBTC. BitGo is trusted to respect the account balances recorded in the smart contract.
There are a few aspects to consider in the WBTC example.
- Single custodian. The bridge for WBTC relies on a single custodian for its integrity. They can issue more WBTC on Ethereum than what is locked in Bitcoin and they can decide not to honour any WBTC withdrawals back to Bitcoin.
- Independent security models. Ethereum has its own security model that is independent of Bitcoin. The bridge has its own security model that is independent of both blockchain networks.
- Ethereum is a sidechain. The transactions have moved off-chain from Bitcoin to Ethereum.
A commonality for all three bridge types is that they do not check the sidechain’s integrity and there is no self-enforcing contingency plan to protect the funds if the custodians (or sidechain) goes offline. They are at the whim of their own security model and not that of the layer-1 blockchain in which the bridge resides.
Hold on. How do layer-2 protocols fit into this article?
The promise of layer-2 scalability is to move transaction throughput from the layer-1 blockchain to another off-chain system. A bridge is required to hold the funds that are issued on the other system.
However, unlike all other bridge types explored in this article, a layer-2 protocol strives to protect the funds with the same security as the layer-1 blockchain and it cannot rely on a set of custodians (or the other off-chain system) to protect the funds.
It requires a new type of bridge:
- Layer-2 bridge. The layer-1 blockchain has custody of the funds and the bridge must be convinced the layer-2 protocol is not compromised. In the worst case, the bridge will self-enforce the layer-2 protocol’s liveness until all funds can be withdrawn.
The layer-2 bridge is the most powerful of all bridges.
It does not rely on a set of custodians to safe-guard the funds. Instead the bridge must be convinced that all is well with the off-chain system before the funds can be released. If for any reason the bridge is convinced the off-chain system is compromised, then the bridge can simply bypass the other network altogether.
This is why layer-2 protocols are so exciting and it has taken several years for the emerging companies to propose a solution. The race to be first-to-market with a layer-2 protocol is mostly focused on how to implement a secure layer-2 bridge (and not necessarily how to implement the other blockchain network).
This is a good opportunity to explore the technical problems and the definition further. We explicitly said the bridge must be convinced the layer-2 protocol is not compromised and the act of being compromised can be broken into four problems:
- Data availability. How is the bridge convinced that all data for the other blockchain network is publicly available such that users can independently recompute the layer-2 database?
- State transition integrity. How do we convince the bridge that all state transitions for the layer-2 network are well-formed and valid?
- Withdrawal integrity. How does the bridge guarantee that all honest users funds can be withdrawn if the layer-2 network is compromised?
- Protocol liveness. How does the bridge guarantee that transactions can still be executed if the layer-2 protocol is stalled or offline?
Of course, the above problems must be solved while the bridge contract has significantly less computational resources than the off-chain system and thus the bridge cannot naively re-execute all transactions in real-time. Otherwise, it is not a scalability solution.
Solving the above problems can lead us down a rabbit hole. This is the world of on-chain challenges, fraud proofs, validity proofs, posting transaction data to the layer-1 blockchain (rollups) and on-chain exodus.
While our article does not focus on the spectrum of solutions, we highlight that all solutions are not equal. Some soon to be deployed layer-2 protocols will not satisfy the above security goals. As a result, it is not fair to say they are layer-2 protocols as they lack a layer-2 bridge.
None of the four bridges are “wrong”
As we have seen throughout the article, there are four types of bridges that allow funds to be locked in one blockchain and for the funds to be represented in another off-chain system (that may very well be another blockchain).
Custodian bridges. The first three bridges focus on which set of custodians have control over the locked funds. The custodian’s role is to verify the off-chain system is correct before permitting any withdrawals from the bridge. It is assumed the off-chain system’s integrity is a client-side problem and the custodians have sufficient computational resources to process it. While there is work to reduce the role of the custodian and to introduce crypto-economic incentives to encourage custodians to follow the protocol, the bridge protocols cannot fully constrain the custodians. There are several examples of bridges who have lost user funds (e.g., MtGo) and this is because the integrity of the bridge ultimately relies upon human trust.
Layer-2 bridges. The bridge replaces the role of custodians for holding custody of the funds and checking the off-chain system’s integrity. At the heart of the problem, the bridge must be convinced the off-chain system is not compromised while it lacks the computational resources to independently check every transaction (otherwise, it is not a scalability solution). Alongside the non-trivial technical challenges this poses, it does not come for free. There is an on-going financial cost to convince the layer-1 blockchain that the off-chain system is indeed well-formed and its integrity is intact. However, the bridge ultimately has custody of the funds and not the off-chain system operators.
Overall, the jury is still out on whether users really care about layer-2 bridges and whether we should extend the security model of Ethereum onto off-chain systems. Like all things in life, I suspect all four bridges are here to stay as they are essential for user adoption.
My only request is for you, the user, to take care and consider the type of bridge used by your favourite protocol. It is important to better understand how your funds are protected against bad actors.









